Last time , I have explained about the Clickjacking attack and prevention. Today, i am going to explain about the Self-XSS(Cross Site Scripting) Attack
What is Self-XSS?Self-XSS is one of the popular Social Engineering Attack used by Attackers to trick users into paste the malicious code in browser. Results in attacker accessing to the whatever website you visit. Usually scammers use this attack for tricking users to buy products or get money through online survey .
Recently, Hackers Attacked Facebook with explicit hardcore porn images. Facebook says it might be self-Xss Attack .
Javascript can be executed in browser url bar.
For example , enter the following code in your browser:
javascript:alert('BreakTheSecurity');
This will show a pop up box with "BreakTheSecurity". An attacker can use this for malicious purpose. He can steal Confidential data, cookies, redirect to malware sites and more.
For Eg:
Entering the following code will display the cookies in your browser:
javascript:alert("Cookies:"+document.cookies+" "+"\n By \n BreakTheSecurity");
The above code is not going to anything maliciously other than displaying the cookies. But an attacker can extend the script so that it can take advantage your data.
Security Tips from BreakTheSecurity:
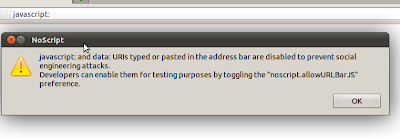
- Use NoScript add on that will prevent javascript running in your browser.
- Don't click the shorthand urls for Example: bit.ly/55ewEb?22. This may redirect to an infected sites.
Aware of Social Engineering:
- If anyone ask you(even if he is your friend) to paste the scripts in browser bar, Never do this mistake.
- If anyone says "Iphone only $10", Don't eager to click it.
- If anyone says "1000 shares will cure a baby", Never do this mistake. Facebook shares never help to get money or help to cure baby.
- Read our EHN spam report to know the latest updates about the facebook scams.


No comments:
Post a Comment